Empowering LEAs with Real-Time Location Intelligence.
The Power Behind Location Intelligence
Vigilo is an AI-powered Location Intelligence Platform for Law Enforcement and Public Safety agencies — turning telecom and mobility data into real-time actionable insights for faster investigations, threat detection and emergency response, with full privacy and chain-of-custody compliance.
Vigilo Core
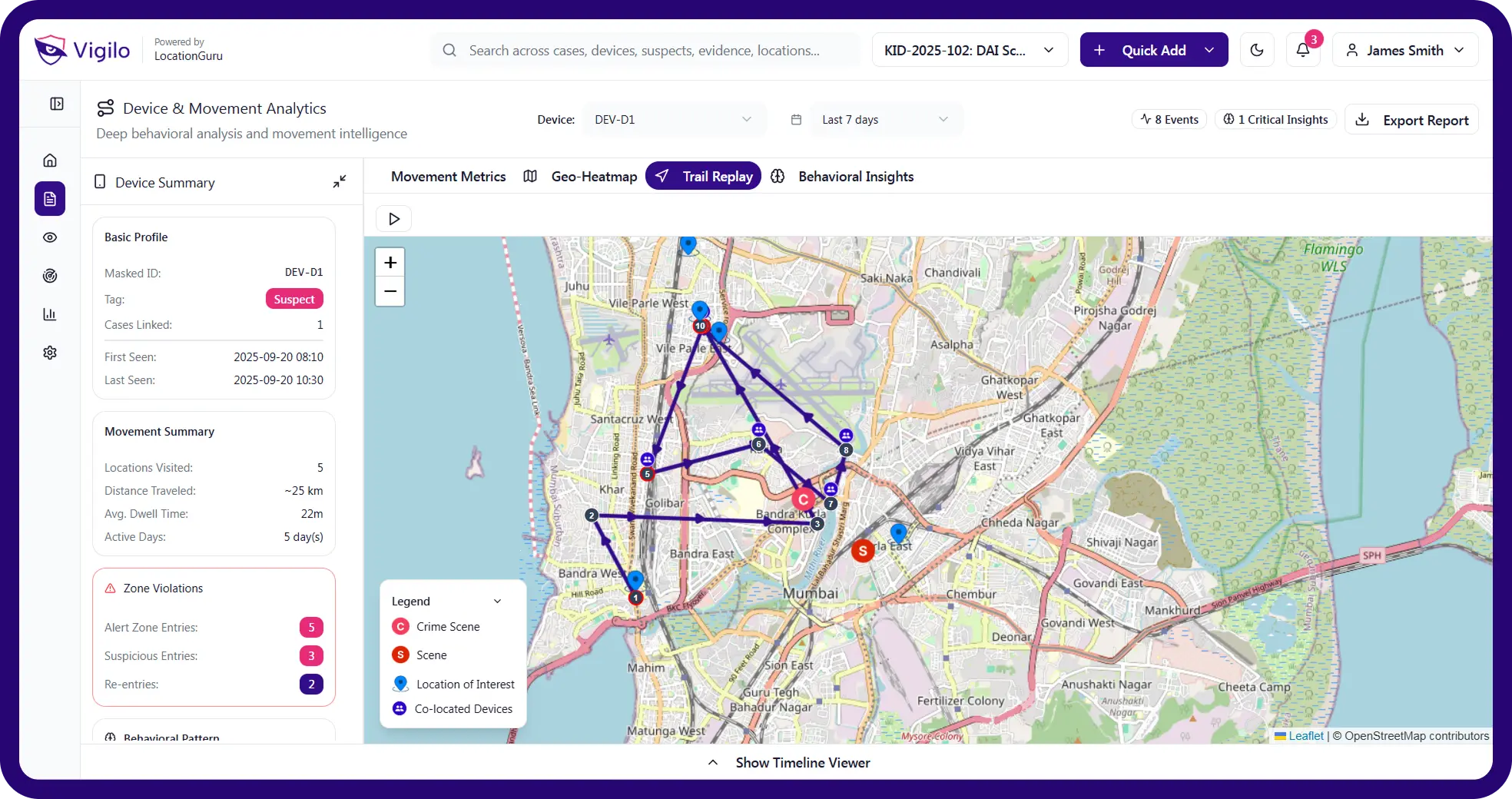
Real-Time & Historical Location Intelligence
Identify live and past movements at the national scale — with privacy-preserved, anonymized data processing.
Mass-Scale Processing
Ingests billions of signalling/CDR events per day with telecom-grade performance.
Real-Time Detection
Instant location lookup & live mobility snapshots for persons of interest.
Movement Intelligence
Continuously tracks direction, speed, and entry/exit flows across zones.
Privacy Security
Built-in anonymization, access control, and secure processing by design.
Vigilo Intel
Real-Time Crowd & Zone Awareness
Designed for real-time monitoring, Vigilo Intel provides situational visibility over zones, events, borders, and sensitive areas through geospatial analytics.
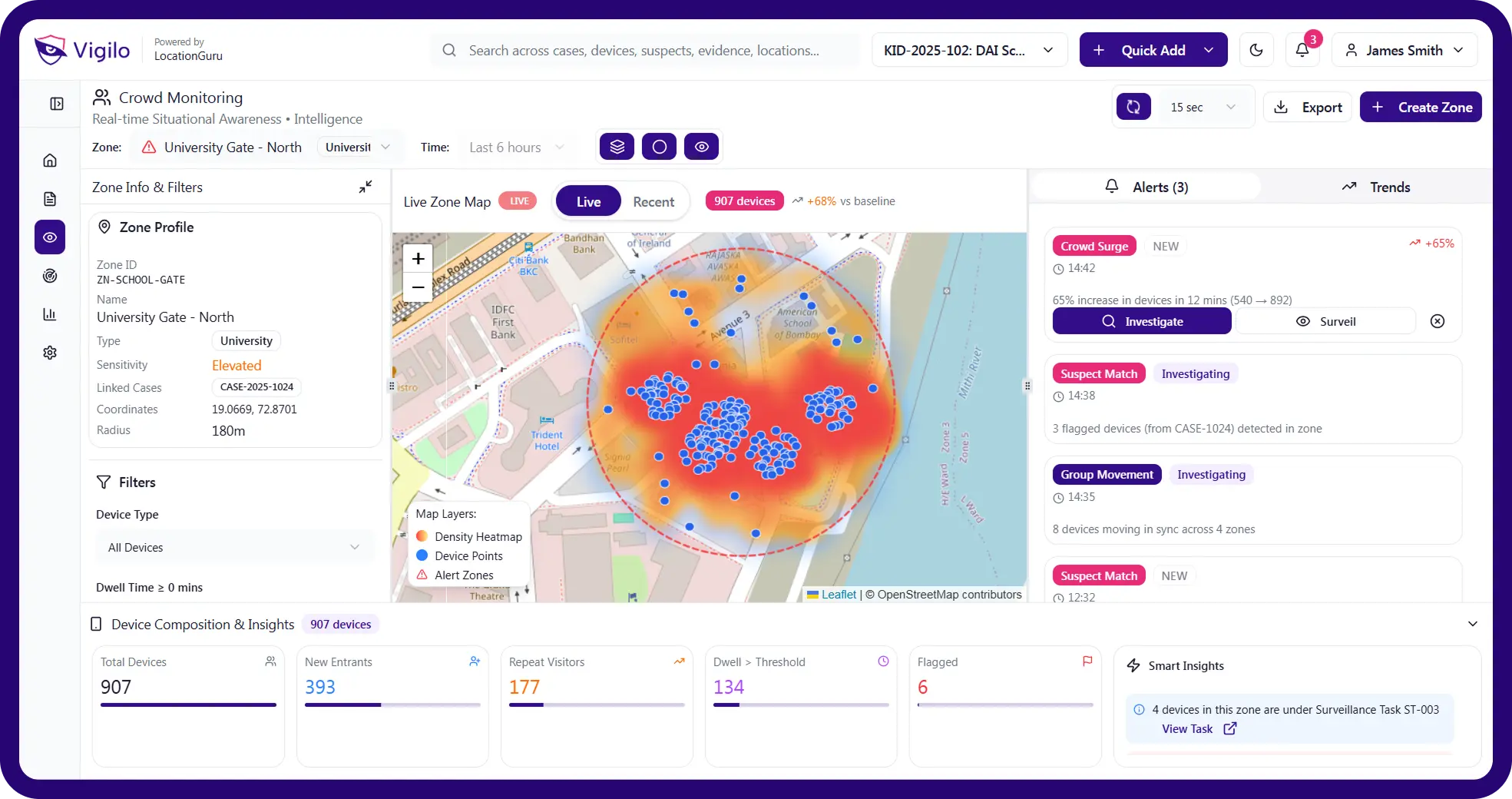
Crowd Monitoring
Detect density spikes, anomalies and movement flows in real time.
Live Geofences
Generate rule-based triggers on areas, events, and watchlist devices.
Trend Analysis
Identify emerging threats or unusual patterns over time.
Predictive Insights
Learn from historical mobility to anticipate risk.
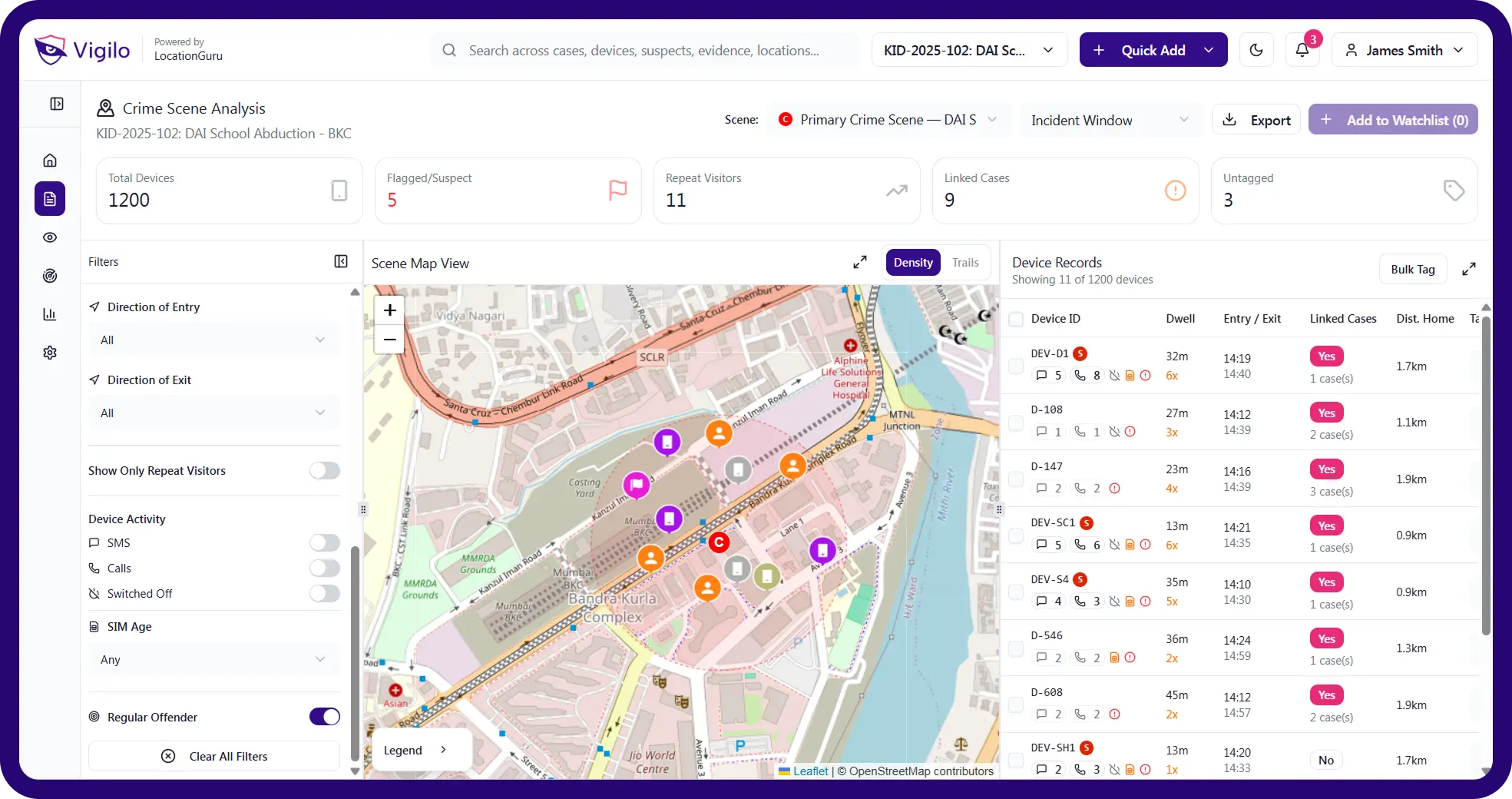
Vigilo Forensic
High-Precision Crime Scene Intelligence
Built for investigators, Vigilo Forensic transforms telecom traces, mobility patterns, and device history into evidence-ready investigative intelligence.
Device Filtering
Apply dwell time, direction & frequency filters on suspects.
Co-location Linking
Surface groups moving or acting together.
Trail Playback
Reconstruct movement paths around incident windows.
Offender Surfacing
Highlight prior involvement from past incidents.
Vigilo Connect
Secure Integration & Data Fusion Layer
Vigilo Connect enables unified access to telecom signalling, CDRs, sensors, command centres, and application systems — with security & audit-ready controls.
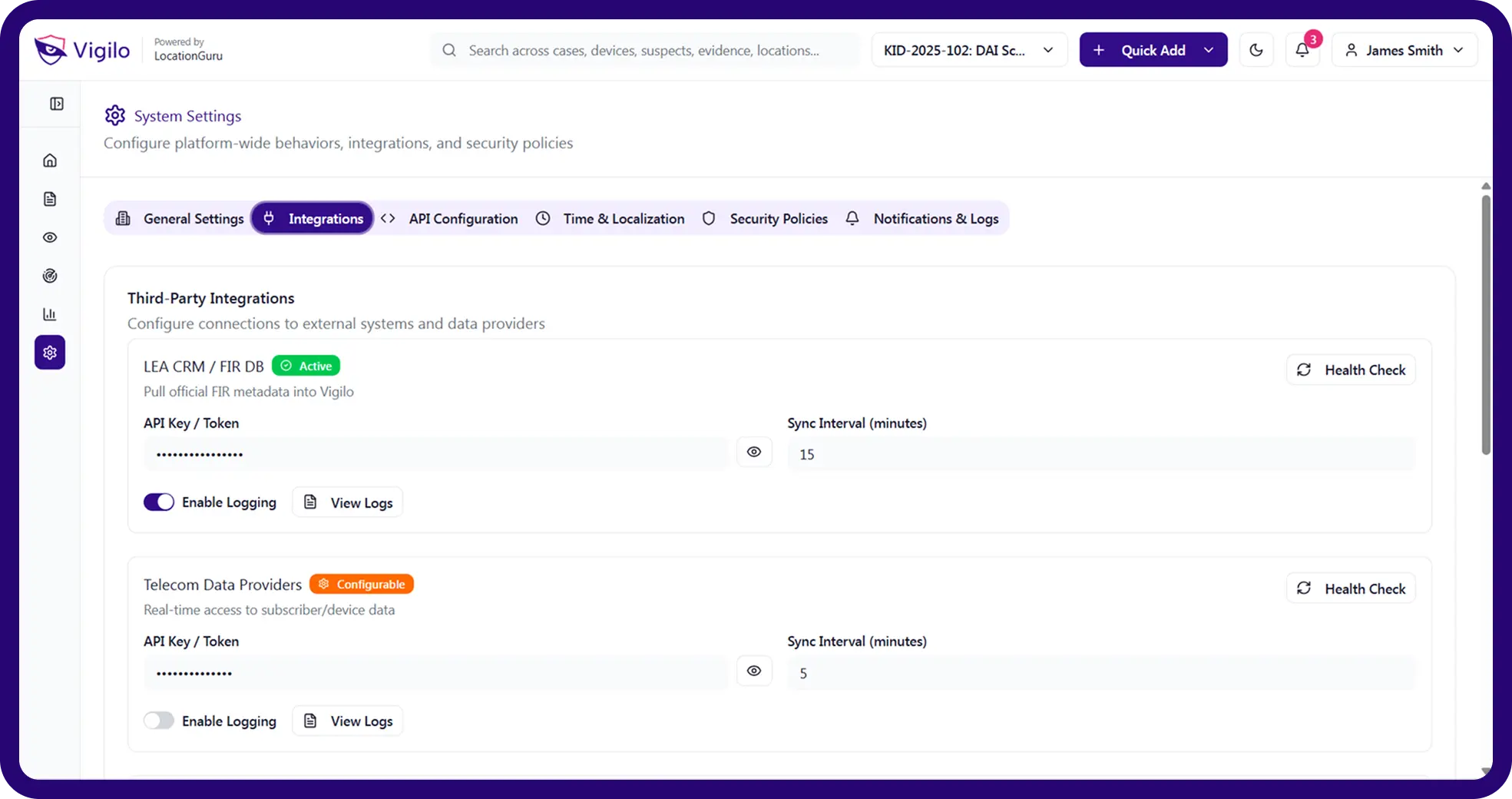
Secure Gateway
Controlled access to telecom cores, LEA apps & command systems.
Agency Integration
Connects multiple LEA systems for unified intelligence flow.
Identity Control
Authentication, role-based authorization & API key governance.
Data Sharing
Securely exchange intelligence across police, border, emergency & national units.